Widziałeś to:
http://technet.microsoft.com/en-us/library/cc730656.aspx
"If you are using a tunnel, specify the endpoints on the Tunnel Settings tab. By default, no tunnel is used. For more information about using tunnels, see IPsec Tunnel Settings. Tunnel rules cannot be mirrored."
->
IPsec Tunnel Settings
Applies To: Windows 7, Windows Server 2008 R2
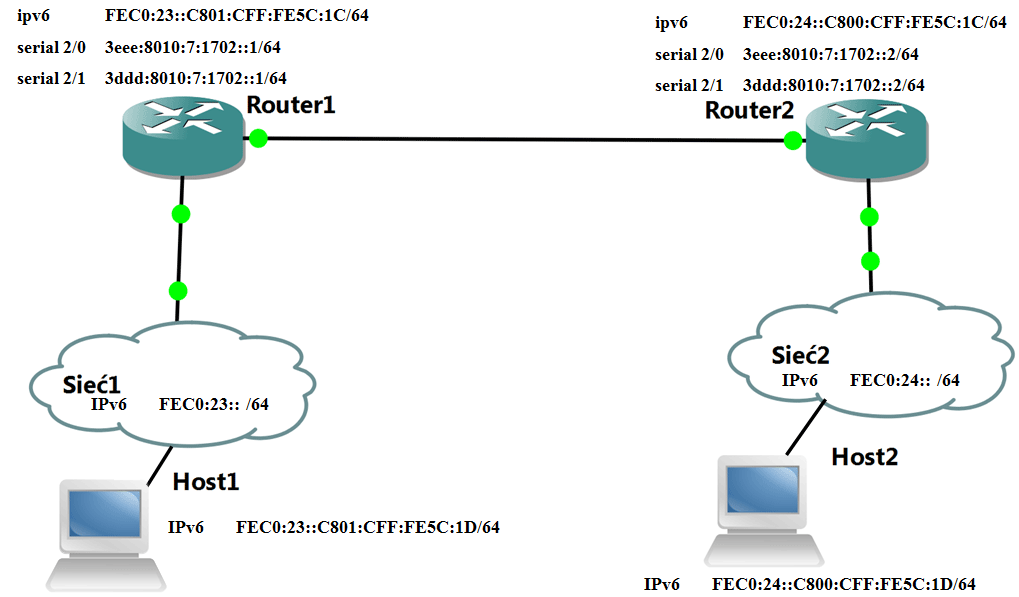
IPsec can perform Layer 3 tunneling for scenarios in which Layer Two Tunneling Protocol (L2TP) cannot be used. If you are using L2TP for remote communications, no tunnel configuration is required because the client and server virtual private networking (VPN) components of Windows create the rules to secure L2TP traffic automatically.
To create a Layer 3 tunnel using IPsec, use the IP Security Policies or Group Policy snap-ins to configure and enable the following two rules for the policy:
- A rule for the outbound traffic for the tunnel. The rule for the outbound traffic is configured with both a filter list that describes the traffic to be sent across the tunnel and a tunnel endpoint of an IP address configured on the IPsec tunnel peer (the computer or router on the other side of the tunnel).
- A rule for the inbound traffic for the tunnel. The rule for the inbound traffic is configured with both a filter list that describes the traffic to be received across the tunnel and a tunnel endpoint of a local IP address (the computer or router on this side of the tunnel).
 Note Note |
|---|
| You must create both an inbound and outbound for each tunnel connection. If a filter is created for only one direction, the rule will not be applied. |
When creating a policy for a computer Windows Vista or a later version of Windows, you can specify either an IPv4 address or an IPv6 address. You must specify an endpoint for each side of the tunnel and the address protocol version must be the same for both sides. That is, if you specify an IPv6 address for the source side of the tunnel, then you must also use an IPv6 address for the remote side of the tunnel.
For each rule, you must also specify filter actions, authentication methods, and other settings.
Po przeczytaniu tego wnioskuję, że Twoje założenia były słuszne. Daj znać koniecznie cz eksperyment ot potwierdzi ponieważ sam jestem bardzo ciekaw.
Może jakieś PrntScrn z podsłuchanego ruchu z opisem. Przyda się przyszłym czytelnikom z podobnym problemem.